The Difference of Server Hardware and Software Firewalls
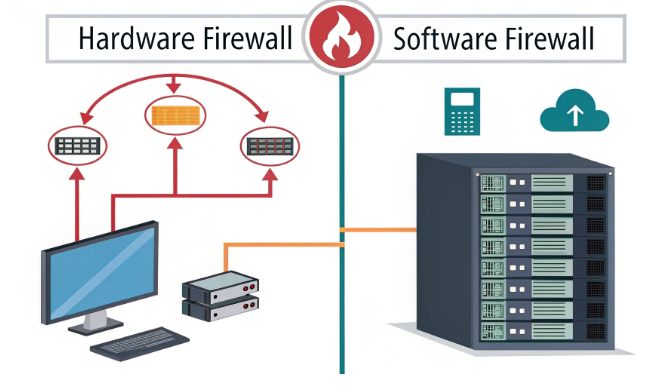
In today’s increasingly complex digital landscape, server protection has become a critical concern for Hong Kong hosting providers and enterprises. With cyber threats growing in both sophistication and frequency, understanding the nuanced differences between hardware and software protection mechanisms is fundamental for implementing robust security architectures. This comprehensive technical guide explores both approaches in depth, providing system administrators and technical professionals with the knowledge needed to make informed decisions about their server security strategy.
Understanding Hardware-based Server Protection
Hardware-based server protection, commonly referred to as “hardware defense,” encompasses purpose-built physical devices engineered specifically for security applications. These specialized appliances operate at the network level, functioning as a formidable first line of defense against various cyber threats. Unlike software solutions, hardware protection operates on dedicated resources, ensuring consistent performance regardless of server load conditions.
Key Components of Hardware Protection
- Enterprise-grade physical firewalls featuring ASIC processors optimized for packet inspection
- Dedicated DDoS mitigation appliances capable of handling multi-vector attacks
- Hardware-based Intrusion Prevention Systems with real-time threat detection
- Load balancers incorporating advanced security features and traffic analysis
- Physical network segregation equipment for enhanced isolation
Software-based Server Protection Explained
Software protection mechanisms operate directly within the server environment or network infrastructure. These solutions offer unprecedented flexibility and can be rapidly updated to address emerging security threats. They typically function at both the application and system levels, providing granular control over security policies while enabling deep packet inspection and behavioral analysis.
Essential Software Protection Components
- Host-based firewalls and IDS/IPS with customizable rulesets
- Web Application Firewalls featuring machine learning capabilities
- Advanced antivirus and malware detection systems with heuristic analysis
- System integrity checkers utilizing cryptographic verification
- Real-time log analysis tools with correlation engines
- Role-based access control systems with multi-factor authentication
Comparative Analysis: Hardware vs Software Protection
When evaluating protection methods for Hong Kong hosting environments, several critical factors warrant consideration:
- Performance Impact:
- Hardware: Negligible impact on server resources, dedicated processing capabilities
- Software: Variable resource consumption depending on configuration and workload
- Deployment Flexibility:
- Hardware: Requires physical installation and configuration, less adaptable to change
- Software: Supports remote deployment, highly configurable with API integration
- Cost Considerations:
- Hardware: Substantial initial investment, predictable long-term maintenance costs
- Software: Lower upfront costs, subscription-based pricing models prevalent
- Update Frequency:
- Hardware: Firmware updates on fixed schedules, longer testing periods
- Software: Continuous updates, rapid threat response capabilities
Technical Implementation Strategies
For optimal protection in Hong Kong hosting environments, consider these detailed approaches:
- Network Layer Protection:
- Implement BGP anycast routing for distributed DDoS mitigation
- Deploy enterprise-grade hardware firewalls at network edges
- Utilize VLANs and microsegmentation for enhanced isolation
- Application Layer Security:
- Configure adaptive WAF rules with custom threat signatures
- Implement intelligent rate limiting and request filtering
- Enable TLS 1.3 with modern cipher suites and perfect forward secrecy
- System Level Protection:
- Implement kernel-level security modules and hardening
- Deploy real-time file integrity monitoring with alerting
- Configure comprehensive endpoint protection solutions
Best Practices for Hong Kong Hosting Environments
- Hybrid Approach Implementation:
- Strategic integration of hardware firewalls with software security tools
- Implementation of defense-in-depth security architecture
- Segregation of management networks with strict access controls
- Security Audit Protocols:
- Regular penetration testing with detailed vulnerability assessment
- Continuous security log analysis and correlation
- Dynamic security policy updates based on threat intelligence
- Compliance Framework:
- Strict adherence to Hong Kong privacy regulations and data protection laws
- Implementation of comprehensive data classification and handling policies
- Maintenance of detailed security documentation and audit trails
Future Trends in Server Protection
- AI-driven threat detection systems with predictive capabilities
- Post-quantum cryptography implementation for future-proof security
- Zero-trust architecture adoption with continuous authentication
- Automated incident response systems with orchestration
- Cloud-native security solutions with container-specific protection
In conclusion, implementing effective server protection for Hong Kong hosting environments demands a sophisticated approach combining both hardware and software solutions. By leveraging the strengths of each protection method while understanding their limitations, technical professionals can architect comprehensive security strategies that defend against both current and emerging threats while maintaining optimal performance and reliability in their hosting infrastructure.

